Next: Copying Information, Previous: All the supported ciphersuites in GnuTLS, Up: Top
This chapter is to give a brief description of the way GnuTLS works. The focus is to give an idea to potential developers and those who want to know what happens inside the black box.
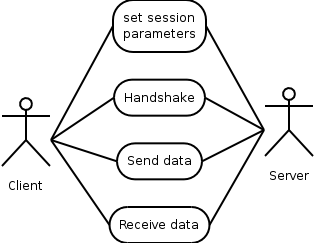
The main needs for the TLS protocol to be used are shown in the image below.

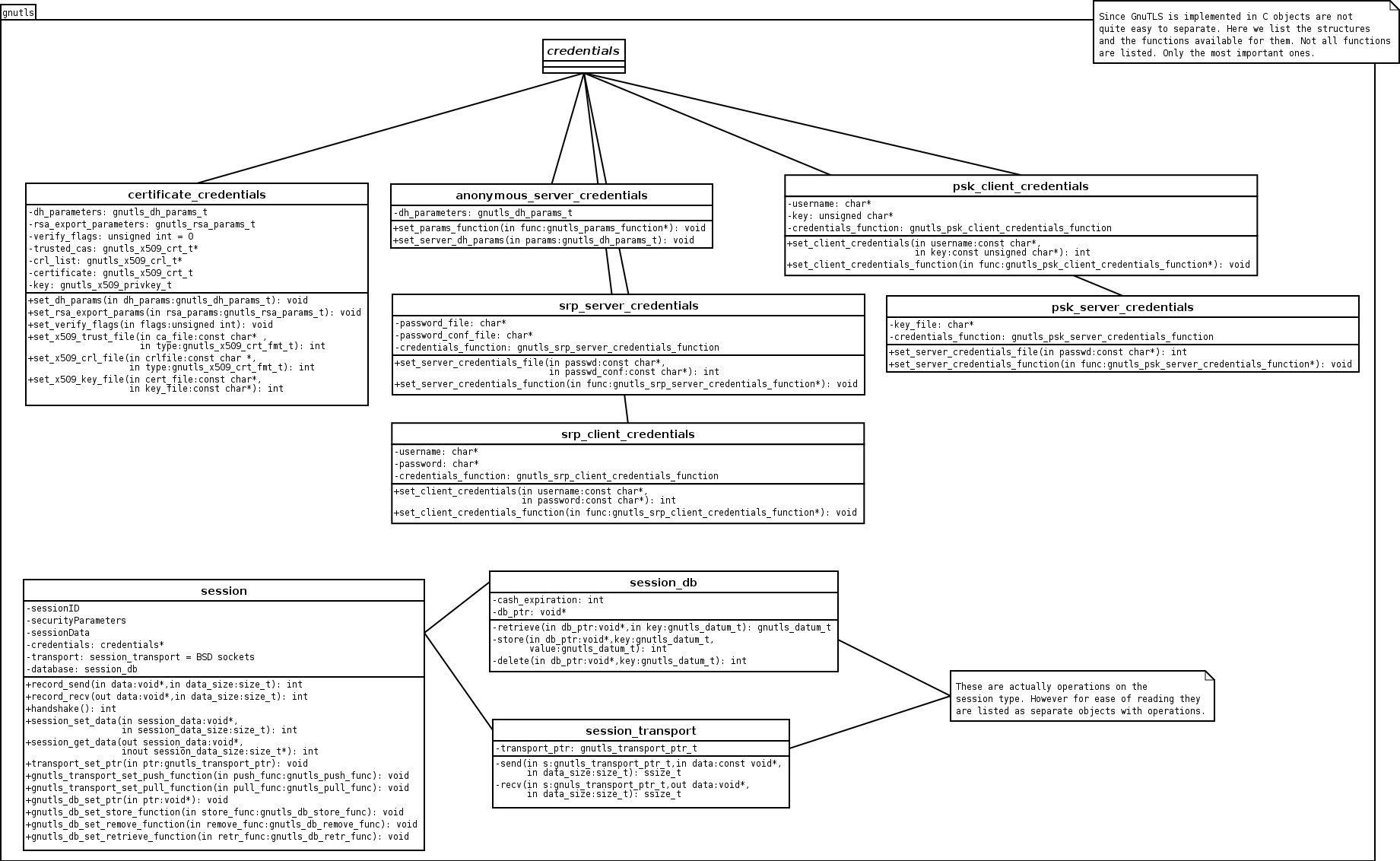
This is being accomplished by the following object diagram.
Note that since GnuTLS is being developed in C
object are just structures with attributes. The operations listed
are functions that require the first parameter to be that object.
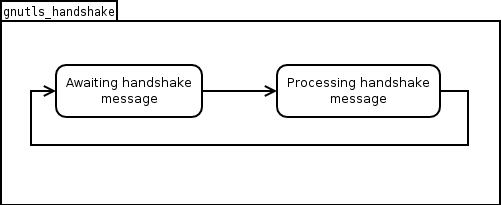
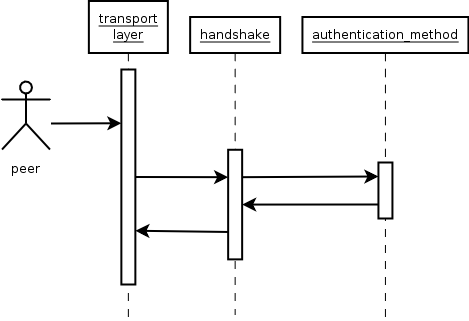
The GnuTLS handshake protocol is implemented as a state machine that waits for input or returns immediately when the non-blocking transport layer functions are used. The main idea is shown in the following figure.
Also the way the input is processed varies per ciphersuite. Several
implementations of the internal handlers are available and
gnutls_handshake only multiplexes the input to the appropriate
handler. For example a PSK ciphersuite has a different
implementation of the process_client_key_exchange than a
certificate ciphersuite.
In GnuTLS authentication methods can be implemented quite easily. Since the required changes to add a new authentication method affect only the handshake protocol, a simple interface is used. An authentication method needs only to implement the functions as seen in the figure below.
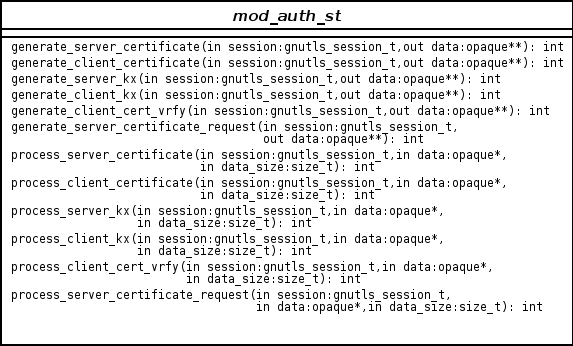
The functions that need to be implemented are the ones responsible for interpreting
the handshake protocol messages. It is common for such functions to read data from
one or more credentials_t structures1 and write data, such as certificates, usernames etc. to auth_info_t structures.
Simple examples of existing authentication methods can be seen in auth_psk.c
for PSK ciphersuites and auth_srp.c for SRP ciphersuites. After implementing these functions
the structure holding its pointers has to be registered in gnutls_algorithms.c
in the _gnutls_kx_algorithms structure.
As with authentication methods, the TLS extensions handlers can be implemented using the following interface.
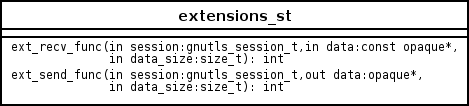
Here there are two functions, one for receiving the extension data and one for sending. These functions have to check internally whether they operate in client or server side.
A simple example of an extension handler can be seen in ext_srp.c
After implementing these functions, together with the extension number they
handle, they have to be registered in gnutls_extensions.c in the
_gnutls_extensions structure.
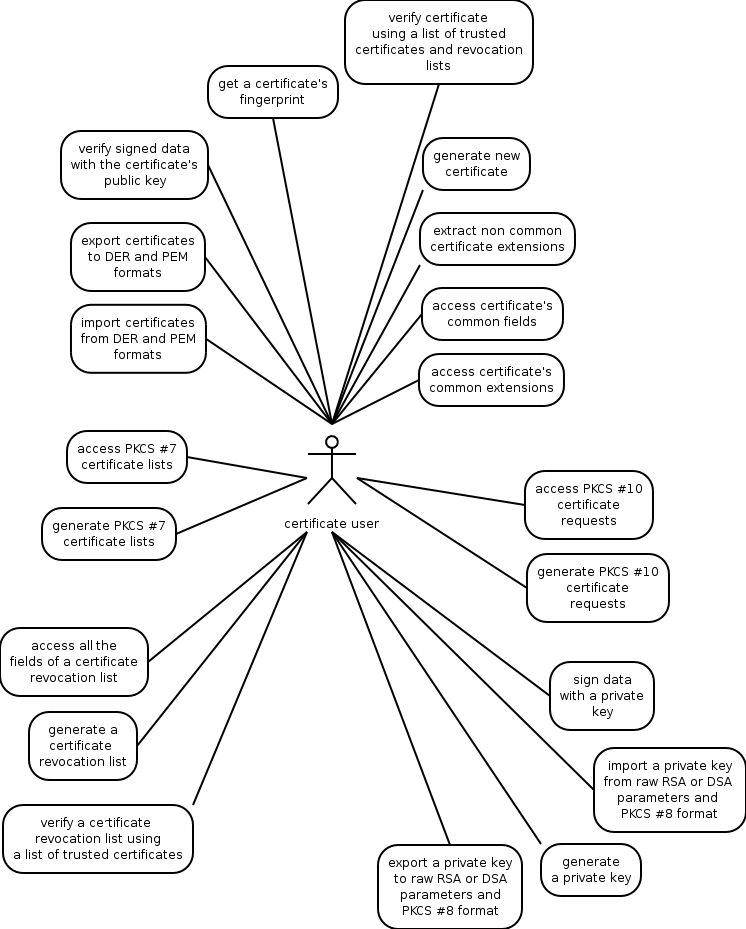
What is provided by the certificate handling functions is summarized in the following diagram.